Breach Breakdown: Shopper Approved
October 12, 2018
The Breach
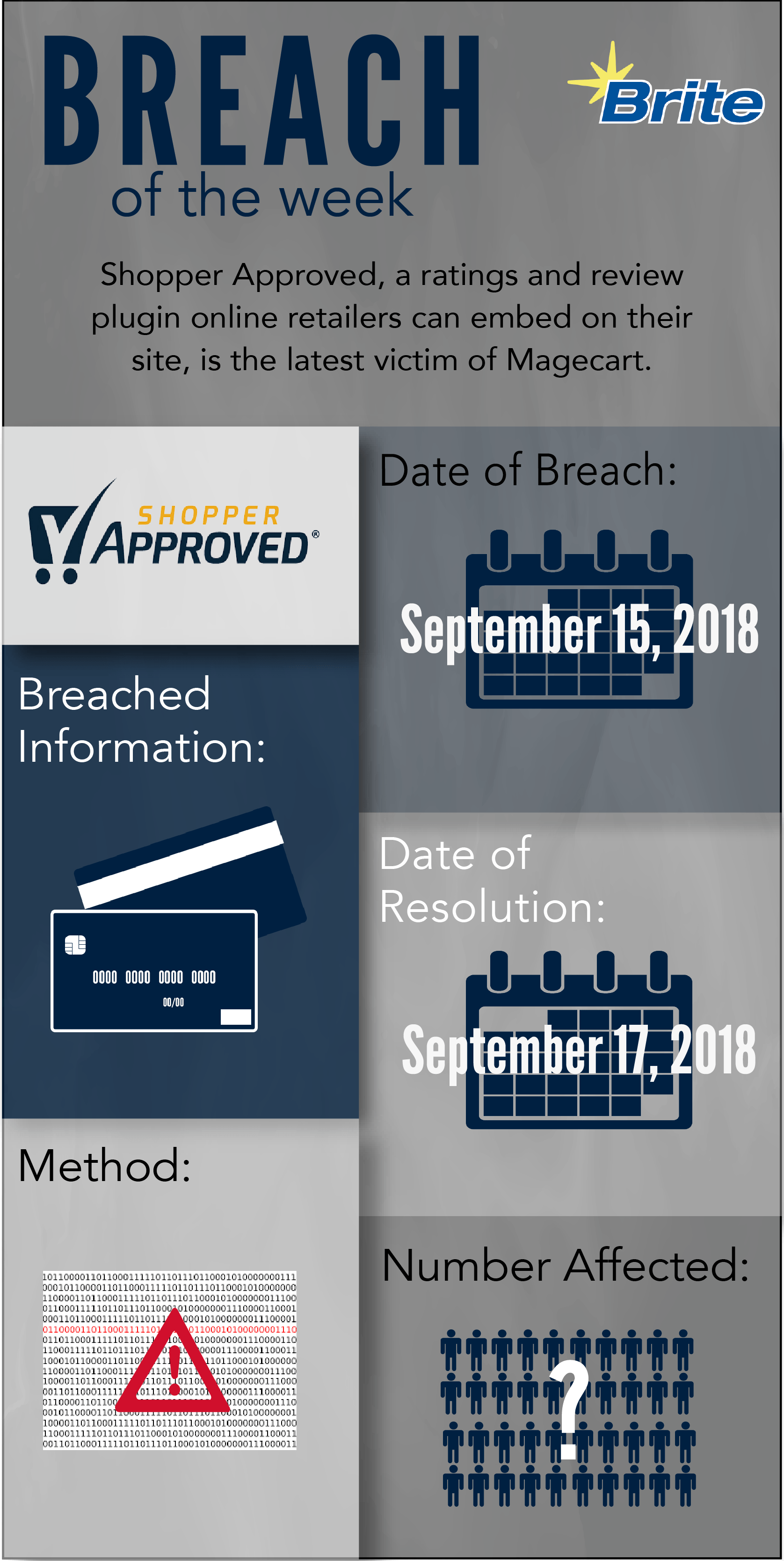
Shopper Approved is the latest Magecart victim. A malicious JavaScript compromised the code of the popular plugin that online retailers can embed their sites to allow customers to post opinions and ratings.
A payment card skimmer code had been added to a legitimate file that collected information entered in checkout forms.
Compared to other Magecart attacks, this had a limited impact. Although Shopper Approved is normally on thousands of sites, the malicious code affected only a small percentage of checkout pages. This is because a majority of the sites that use Shopper Approved did not have the widget embedded on the checkout page. Additionally, the skimmer code only prompted pages that included certain keywords in the checkout URL.
The malicious code was added on September 15. RisqIQ, a cybersecurity firm that has been monitoring the activity of Magecart, detected the infection and contacted Shopper Approved. Shopper Approved removed the code two days later on September 17.
Magecart 101
Magecart is a not a single group of hackers but rather a term that has been given to several hacker groups that operate by a similar pattern by planting payment card-stealing code on legitimate sites.
The threat group has digitized the method of card skimming. Traditionally, card skimmers are hidden within card readers on machines such as ATM’s and fuel pumps. The skimmer steals credit card data later allowing the criminal to use themselves or sell to third parties.
Magecart adds scripts designed to steal sensitive data that consumers enter into online payment forms on e-commerce sites. Scripts are added either directly to the site or through the site’s third-party suppliers. Magecart custom codes are meant to blend seamlessly with the website to avoid detection.
The list of hacks Magecart is responsible for continues to grow. The publicly known attacks include: Ticketmaster, British Airways, Feedify, ABS-CBN, Newegg, Stein Mart, Five Below, and Plant Therapy.

Posted in Cybersecurity Technology