Challenge
Legacy System Compatibility
Solution
Comprehensive Assessment and Modernization Strategies

The Brite Way
Our experts thoroughly analyze your existing systems, developing a customized modernization plan that preserves critical functionalities while leveraging Azure's advanced capabilities.
What Cloud Migration Solutions Does Brite Provide?
Azure Assessment and Planning
A comprehensive evaluation of your current infrastructure and detailed migration roadmap.

Workload Migration
Seamless transfer of applications, databases, and virtual machines to Azure.

Cloud Optimization
Fine-tuning your Azure environment for peak performance and cost-efficiency.
Managed Azure Services
Ongoing support and management of your cloud infrastructure post-migration.
Challenge
Data Security and Compliance
Solution
Robust Security Measures and Compliance Frameworks

The Brite Way
We implement industry-leading security protocols and maintain strict compliance standards throughout the migration process, safeguarding your sensitive information and maintaining regulatory adherence.
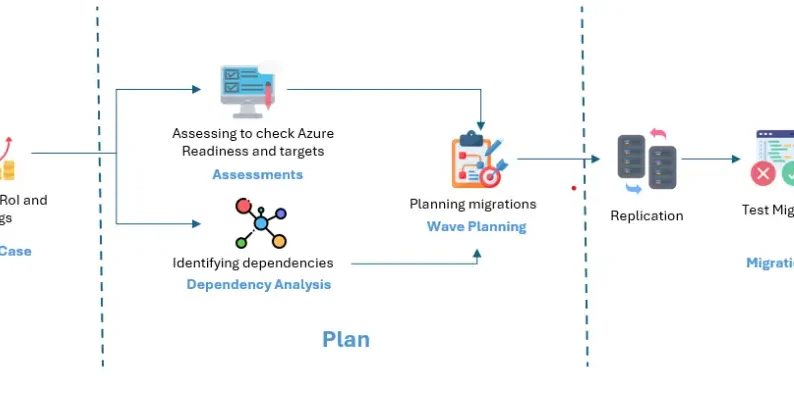
Migration Services
Assessment, Advisement, and Planning
Comprehensive evaluation of existing infrastructure and development of a detailed migration roadmap to Azure.
Server Migration
Seamless transfer of server workloads, including applications and databases, to the cloud platform.
Workload Migration
Efficient transition of applications, databases, and virtual machines from legacy systems to Azure's scalable environment.
Management & Optimization
Ongoing support, fine-tuning, and management of infrastructure for peak performance and cost-efficiency post-migration.
Driving Exceptional Results
Challenge
Business Disruption & Downtime
Solution
Carefully Orchestrated Migration Strategies

The Brite Way
Our step-by-step strategy and advanced migration tools are designed to minimize disruptions to your regular tasks. We focus on off-peak transitions and use parallel environments to ensure seamless business continuity during the migration process.
Ready to Define Your Cloud Strategy?
Contact our expert Microsoft team to assess your objectives and explore the benefits of moving your applications to the cloud with a workload-centric approach.
Cloud Migration Insights & Resources

New York SHIELD Act Compliance Tips
At the beginning of the year, we talked about the New York SHIELD Act compliance and the steps companies had to take. In the shuffle of recent events, the compliance date has come and gone for many without the proper actions in place. With the coupling of legal implications of non-compliance and the developing security vulnerabilities from…

3 Critical Services Every MSP Should Offer
Managed security providers vary vastly with how they do business and what they offer. It is often challenging to compare providers if you are in the market for an MSP. On the surface, most MSPs offer a basic level of IT management and help desk. When you dig a little deeper, comparing providers is really…

Forescout 8.2 Deep Dive: Cloud-First Deployments
Forescout’s 8.2 update introduced a handful of highly anticipated features including a new web-based interface with dashboard upgrades and the eyeExtend Connect App ecosystem. The final feature we want to breakdown in the Forescout 8.2 update is the cloud-first deployment capability. Before 8.2, device visibility and control were limited for organizations with a cloud-first approach,…

New York SHIELD Act: Everything You Need to Know
Yesterday, we teamed up with RDG+ Partners and Harter Secrest and Emery LLP to explore how business will be affected by the New York SHIELD Act. In case you couldn’t make it, or want the highlights, here’s a recap and the biggest takeaways. Rundown of the New York SHIELD Act. First, let’s understand the SHIELD Act. It stands for ‘Stop…

The Challenge of Securing Hybrid Clouds and SDDC’s
With the advancement of technology, it has never been easier for organizations to expand their datacenter. This has been made possible by the introduction of public cloud computing and the Software-defined Data Center (SDDC). However, with this ease of use and network sprawl an inherit Cybersecurity issue has arisen. Securing these methods of computing has…


