Challenge
Internal Network Vulnerabilities
Solution
Automated Penetration Testing

The Brite Way
By employing automated pen testing methodologies, Brite efficiently identifies vulnerabilities in your internal environment, providing detailed reports within 48 hours to help you fortify your defenses swiftly.
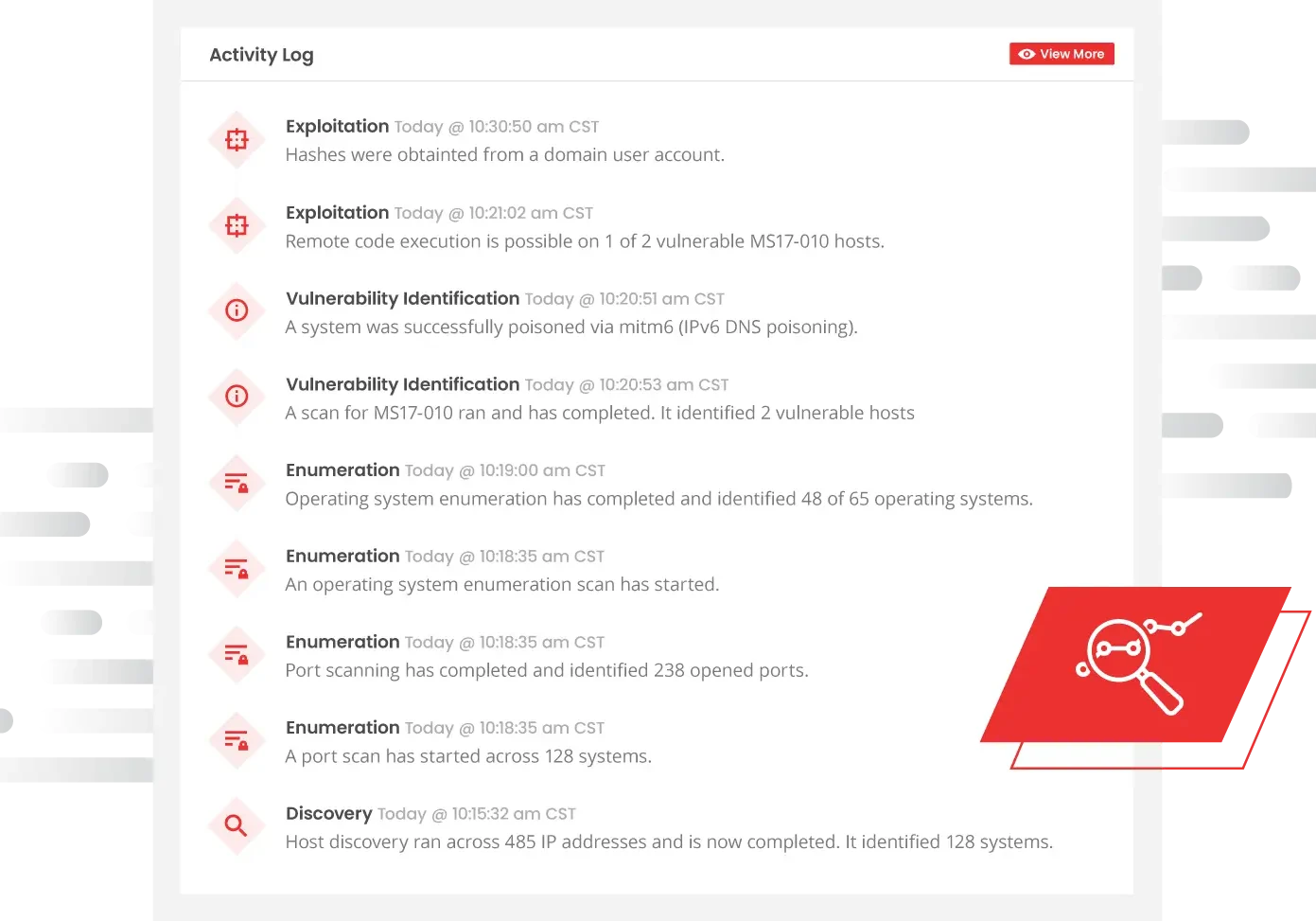
How Does Brite’s Penetration Testing Work?
General Overview
Automated Pen Testing combines multiple methodologies that were once manually conducted into an automated fashion to provide maximum value to organizations.
Target: Internal Network
Using a device connected to your internal environment, our consultants will discover security vulnerabilities present within the internal network environment. These activities simulate that of a malicious attacker.
Target: External Network
Assuming the role of a malicious attacker from the public Internet, our consultants will identify security flaws within your external network environment. These flaws can include patching, configuration, and authentication issues.
Challenge
Network Security Flaws
Solution
Simulated Real-world Attacks

The Brite Way
Brite's approach combines automated testing with expert analysis, ensuring rapid identification of vulnerabilities and delivering actionable insights to enhance your internal and external network security.
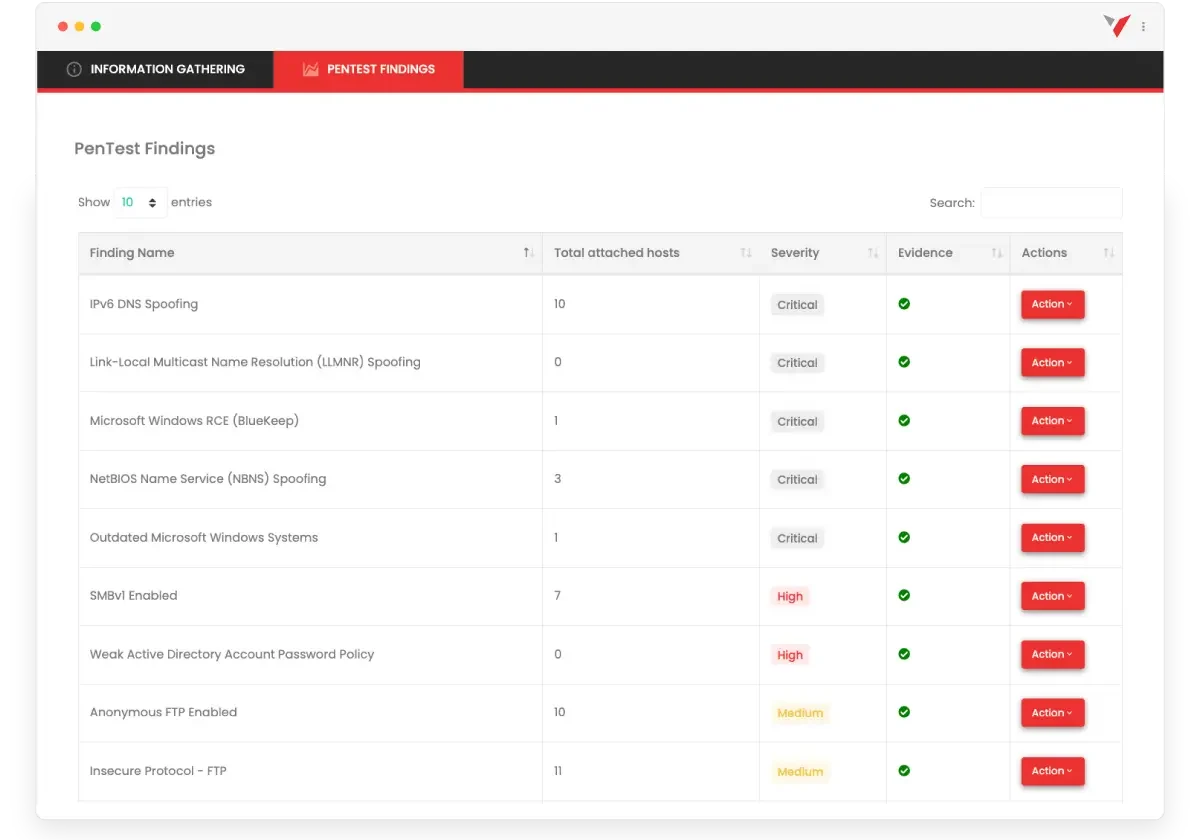
Penetration Testing Services
Egress Filtering Testing
Evaluates the effectiveness of outbound traffic controls to prevent unauthorized data transmission and communication with malicious entities.
Data Exfiltration
Simulates attempts to extract sensitive information from your network, testing your defenses against unauthorized data removal.
Authentication Attacks
Assesses the strength of your authentication mechanisms by attempting to bypass or compromise login credentials and access controls.
Simulated Malware
Replicates malware behavior to test your network's ability to detect and respond to potential infections without using actual malicious code.
Privilege Escalation & Lateral Movement
Examines your system's resilience against attempts to gain higher-level permissions and move between different network segments.
Reports Available Within 48 Hours
Delivers comprehensive vulnerability assessment results and remediation recommendations within two business days of test completion.
Driving Exceptional Results
Challenge
Data Exfiltration Risks
Solution
Egress Filtering Testing and Simulated Data Exfiltration

The Brite Way
Brite's unique methodology simulates sophisticated attacks, including privilege escalation and lateral movement, providing a thorough assessment of your security posture.
Find Out More About Our Penetration Testing Services Today
Penetration Testing Featured Resources

Penetration Testing: What it is and Why Your Organization Needs it
At a Glance: Even with security measures in place, vulnerabilities within an organization’s cybersecurity infrastructure can go undetected. By simulating real-world attacks, penetration testing helps uncover weaknesses before cyber criminals can exploit them. Brite offers comprehensive penetration testing services that help identify and address potential security weaknesses. At Brite, we believe that good enough…

CVE Management: Removing CVEs Swept Under the Rug
IT leadership builds and manages strong, diverse teams to ensure secure and stable operations. However, sometimes departments overlap resulting in confusion and miscommunication. Such is the case with networking and security departments when it comes to CVE management. It is important to address responsibility early on. Who should be held accountable for any unpatched known…

Understanding Risk-based Vulnerability Management
Devices, tools and users are constantly being added to your network and widening the attack surface. Every new addition adds another possibility for misconfiguration and vulnerabilities. The longer a vulnerability goes undetected, the greater the risk. Sound familiar? Security teams across industries all live this reality every day. That’s where risk-based vulnerability management can help.…

Why Organizations Should Look at Penetration Testing
Today’s blog is brought to you by Todd Palma. Todd brings over a decade of technology sales experience to Brite. Through working with organizations of all shapes and sizes, he has been able to identify and respond to market place trends. Hackers and cyber thieves are getting more creative every day in an effort…



