Healthcare breaches: The epidemic people aren’t talking about
March 27, 2019
And within the last month…
Mar. 20, 2019 – Zoll Medical: 277,319 patients personal information was exposed
Mar. 4, 2019 – Rush System for Health: 45,000 patients personal data compromised
Feb. 22, 2019 – UConn Health: more than 326,000 patients personal data compromised
Feb. 20, 2019 – UW Medicine: 974,000 affected patients in a hacking incident
The epidemic.
The healthcare industry has a rapidly growing vulnerability that is being taken advantage of impacting millions of people every day. Healthcare organizations are not securing IT environments, leaving patient information susceptible for hackers to exploit. And the problem is continuing to get worse.
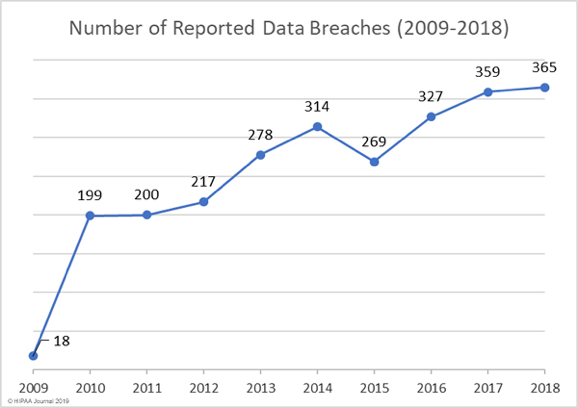
”Between 2009 and 2018 there have been 2,546 healthcare data breaches involving more than 500 records. Those breaches have resulted in the theft/exposure of 189,945,874 healthcare records. That equates to more than 59% of the population of the United States. Healthcare data breaches are now being reported at a rate of more than one per day.”
Why healthcare?
It’s simple. Data is money. And healthcare records are the bank vault of data. All healthcare facilities require basic, personal information upon arrival – name, address, date of birth, and possibly social security number – all of which can be used for identity theft. Healthcare records become even more valuable because records also include confidential medical history, insurance and financial information. Those records can then be used for insurance fraud or to purchase pharmaceutical drugs. At the end of the day hackers are focused on any information that can turn a profit and conveniently healthcare files have less security than the Mona Lisa.
The problems.
There are two main problems for the data breach epidemic – a lack of security and training.
Problem: Lack of security
A reason for the growing attack issue is the growing utilization of IoT devices. These devices include things such as phones, printers, vending machines and medical devices. Projections estimate that by 2020, 40% of IoT technology will be health related. When any of these devices connect to the network, a hacker can then use the device as a gateway into the system and from there navigate to the desired data. Not knowing what unsecured devices are on the network creates a huge gap in the security.
Solution: Visibility
Gain visibility. Doctors don’t just treat without an exam or running tests and scans to understand what is going on. The same applies for cybersecurity. It’s critical to know what devices are on the network and then a proper security plan can be developed. In today’s data and device driven world, a homogeneous approach is not enough. Not all devices contain the same information and therefore don’t require the same level of security. Products such as Forescout provide real-time visibility to actively enforce cybersecurity policies. Detect devices as they connect to the network, restrict access of non-compliant devices and advanced threat detection solutions can isolate an infected system.
Problem: No training
Research indicates that healthcare employees are extremely susceptible to phishing attacks. A combination of high turnover rates and a lack of security training contribute to employees clicking on malicious links and ultimately giving hackers access. While anyone at the company can be targeted, phishing attacks look for privileged accounts that have access to multiple systems across the network. This allows for easier access to confidential information.
Solution: Educate employees
Creating a cybersecurity culture is equally as important as implementing the security itself. Imagine building a gate but not teaching anyone how to use the lock. Start by teaching employees the role they play in cybersecurity. Establish why it’s important, how it can impact them and what they can do to prevent it. For more tips, check out this blog on how to create a cybersecurity culture.
Healthcare organizations need to fully assess current cybersecurity plans and improve upon them to fit the growing concerns of the current day. Brite is ready to help your organization begin that process today. Contact us here.

Posted in Cybersecurity Technology, Security (Legacy)
