During the holiday season people are rushing around scooping up the latest tech gadgets for loved ones (or occasionally themselves). The focus on is on seeing a person’s face light up when they unwrap that perfect gift. No one is thinking of the possible personal or corporate vulnerability it may cause. Keep that in mind as you reach for that latest connected device.
Blog post by Roman Zaikin, Dikla Barda and Oded Vanunu posted on 2017/10/26 by Check Point
The second season of award-winning TV thriller Mr. Robotpremiered with a scene that sent shivers down the cybersecurity world’s spine. In uncomfortably realistic detail, hackers virtually broke into a smart home, turning the home-based IoT technology against its inhabitants. The TV and stereo started switching on and off randomly, the water temperature in the shower went from boiling to freezing with little warning, and the air conditioning brutally forced the characters to leave their homes by reaching arctic temperatures. The most unsettling part of the whole sequence isn’t that this type of cyberattack might happen.
It’s unsettling because it’s already happening.
Recently, Check Point discovered vulnerability, dubbed HomeHack, in LG’s smart home infrastructure exposing it to critical user account takeover. If attackers would have exploited this vulnerability, , they would have been able to log into LG users’ SmartThinQ® home appliances accounts and take remote control of the devices connected to the account.
The HomeHack vulnerability gave attackers the potential to spy on users’ home activities via the Hom-Bot robot vacuum cleaner video camera, which sends live video to the associated LG SmartThinQ app as part of its HomeGuard Security feature. Depending on the LG appliances in the owner’s home, attackers could also switch dishwashers or washing machines on or off.
This vulnerability could have been widespread: sales of the LG Hom-Bot robotic vacuum cleaner alone exceeded 400,000 in the first half of 2016.
We notified LG about this vulnerability on July 31 2017, and LG responded responsibly to stop possible exploitation of the issues in its SmartThinQ app and devices, releasing a new version patching this vulnerability at the end of September.
To learn more about the latest advances in securing the Internet of Things, download the “Enabling the IoT-connected world through cybersecurity” white paper.
LG is a leading provider of industrial, enterprise and home appliance IoT Devices. It launched the SmartThinQ® line of home appliances in 2011, allowing users to monitor and maintain their homes anytime and anywhere, by remotely controlling them via an app. These smart devices include commonly used items such as dishwashers, refrigerators, microwaves, dryers, and robotic vacuum cleaners.
Dust of Privacy – Hacking the Hom-Bot
One of LG’s SmartThinQ appliances is the Hom-Bot vacuum cleaner. The company presents it as a hybrid between a vacuum cleaner and a watch guard, with HomeGuard security that can send out alerts when it detects movement. This function is designed to enable users to turn on the built-in video camera positioned on top of the Hom-Bot vacuum, which then provides a real-time video stream to the smartphone application.
TO WATCH A DEMO OF THE ATTACK – CLICK HERE
However, this camera, in the case of account takeover, would allow the attacker to spy on the victim’s home, with no way of them knowing, with all the obvious negative consequences of invasion of privacy and personal security violation.
We discovered the HomeHack vulnerability residing in the login process of the user signing into their account on the LG SmartThinQ app.
First, the attacker needs to recompile the LG application on the client side, in order to bypass security protections. This enables the traffic between the appliance and the LG server to be intercepted. Then, the would-be attacker creates a fake LG account to initiate the login process. By manipulating the login process and entering the victim’s email address instead of their own, it was possible to hack into the victim’s account and take control of all LG SmartThinQ devices owned by the user, including the Hom-Bot robot vacuum cleaner, refrigerators, ovens, dishwashers, washing machines and dryers, and air conditioning units.
This vulnerability highlights the potential for smart home devices to be exploited, either to spy on home owners and users and steal data, or to use those devices as a staging post for further attacks, such as spamming, denial of service (as we saw with the giant Mirai botnet in 2016) or spreading malware.
As more and more smart devices are being used in the home, hackers will start to shift their focus from targeting individual devices, to hacking the apps that control networks of devices. This will give criminals even more opportunities to exploit software flaws, cause disruption in users’ homes and access their sensitive data.
As such, users need to be aware of the security and privacy risks when using their IoT devices and it’s essential that IoT manufactures focus on protecting smart devices against attacks by implementing robust security during the design of software and devices – rather than adding security later as an afterthought.
Protecting against HomeHack
To protect their devices, users of the LG SmartThinQ mobile app and appliances should ensure they are updated to the latest software versions from the LG website. Check Point also advises consumers to take the following steps to secure their smart devices and home Wi-Fi networks against intrusion and the possibility of remote device takeover:
- Update LG SmartThinQ app to the latest version (V1.9.23), you can update the app via Google play store, Apple’s App Store or via LG SmartThinQ app settings.
- Update your Smart home physical devices with the latest version, you can do that by clicking on the smart home product under smartThinQ application Dashboard (if an update is available you will get a popup alerting you)
HomeHack Technical Details:
In the process of exposing this vulnerability, we looked into LG’s Phone application and the backend platform. To be able to use debugging tools, we used a rooted device. Initially, we encountered a root detection feature, which causes the LG application to immediately close if it detects the phone is rooted.
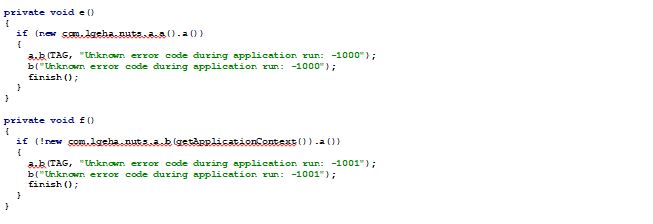
Our first step was to bypass this anti-root mechanism. Using an ADB (Android Debug Bridge) tool, we pulled the application and decompiled it. Looking at the code, we revealed two functions that are responsible for the root detection:
As you can see, both functions call finish to execute onDestory method, which closes the application.
To bypass this mitigation, we simply removed the “finish” calls and recompiled the application.
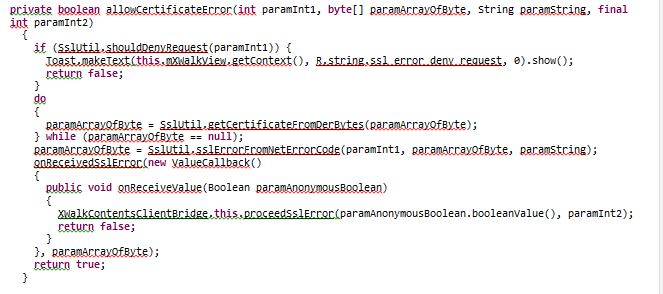
After bypassing the root detection, we setup a proxy which allowed us to intercept the application traffic. At first, we encountered an SSL pining mechanism, which prevented us from intercepting the application traffic and investigating it.
Then, we went back to the code to learn how LG implemented the SSL pinning mechanism:
We patched this function and recompiled the application again, this time adding to it debugging capabilities. By removing all obstacles, we achieved the traffic interception.
Our next step was to create an LG account and log into the application. By analyzing the login process, we found that it contains the following requests:
- Authentication request – verifies user credentials.
- Signature request – creates a signature based on the username from authentication request.
- Token request – use the signature response as a header and username as parameter to get access token for the user account.
- Login request – sends the access token in order to login to the application.
We found that there is no direct dependency between step 1 and steps 2-3. This means that the attacker could use his username to pass step 1, and then change the username to the victim’s in steps 2 and 3. Step 4 would allow the attacker to complete the login process to the victim’s account.
By exploiting the HomeHack vulnerability, as described above, the attacker could take over the victim’s account and control his smart LG devices.
How it all started:
When we first started our investigation, we initially looked into the Hom-Bot itself and searched vulnerabilities in the device itself. We disassembled the Hom-Bot to find the UART (Universal Asynchronous Receiver/Transmitter) connection.
This gave us access to the filesystem. The UART connection can be found on top of the camera near the label console. By connecting to the UART, we managed to manipulate the U-Boot and receive access to the filesystem.
While debugging the main process, we looked for the code responsible for Hom-Bot’s communication with the SmartThinQ mobile application.
This is when we had the idea to investigate the SmartThinQ application – leading to the discovery of the HomeHack vulnerability, which turned the Hom-bot to Hom-Spy.
To learn more about IoT security and how to secure your networks, click here.