Challenge
Evolving Threats
Solution
Multi-Layered Detection

The Brite Way
Our proactive approach combines advanced threat intelligence with continuous monitoring, ensuring that your defenses adapt to the latest threats and vulnerabilities.
Why Advanced Threat Protection with Brite?
Proactive Defense vs Reactive Recovery
We help you get ahead of complex, advanced threats by creating a strong, adaptable defense. It is much easier and more cost-effective to prevent an attack than to recover from one.
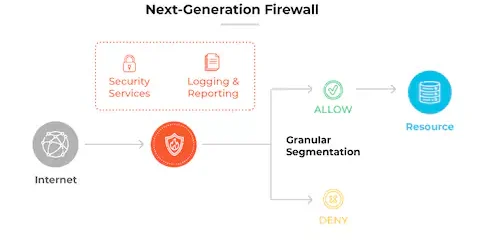
Defend the Attack Surface
Our team defends your organization's attack surface by identifying and mitigating vulnerabilities, reducing the risk of security incidents, and increasing your ability to respond to and recover from attacks.
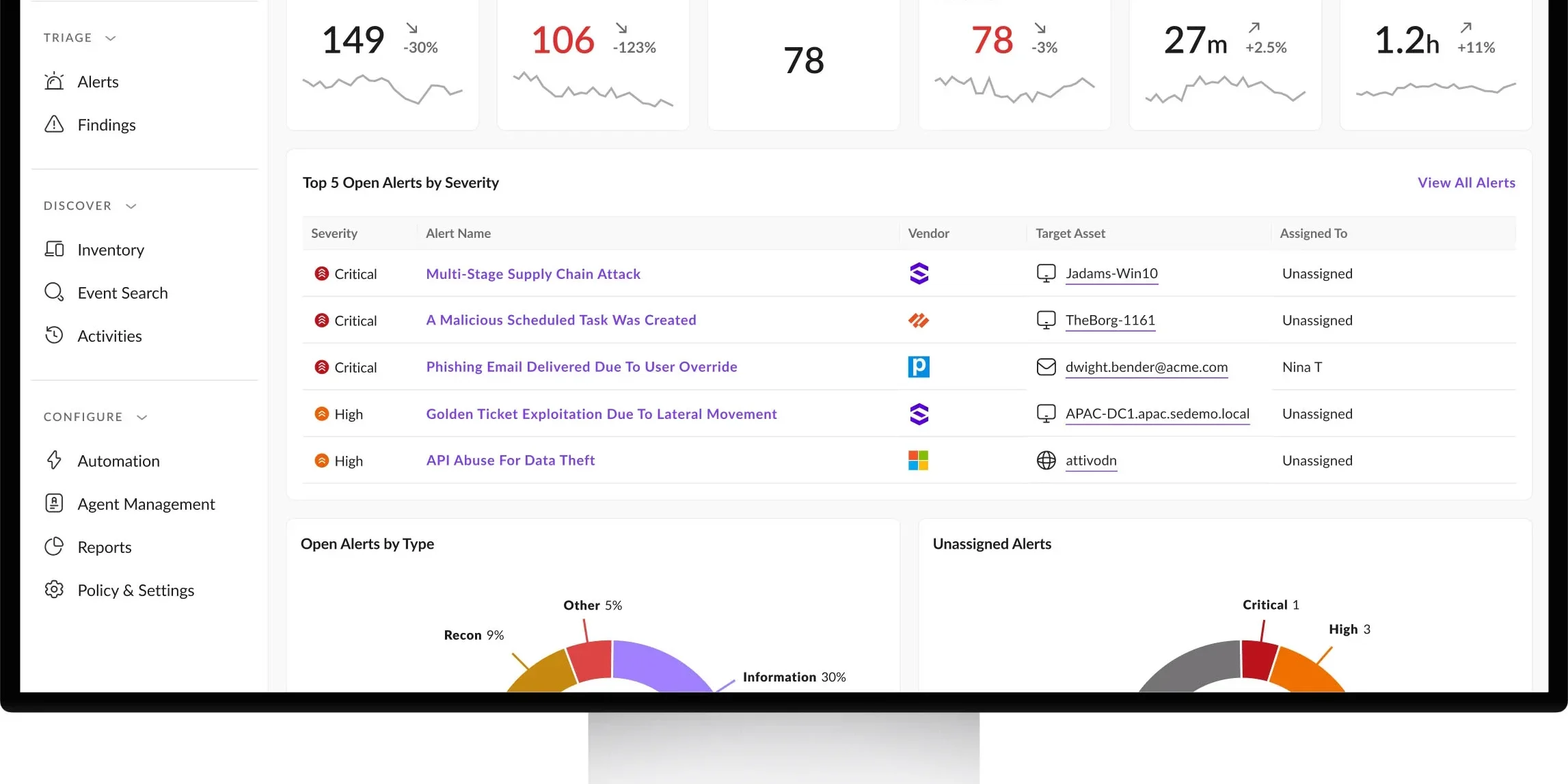
Centralized Context & Correlation
Cyber attacks are complex with many different aspects to consider. Our ATP service enables centralization, cross-source context, and correlation of information for better defense and quicker response.
Challenge
Alert Fatigue & Tool Mismanagement Slowing Response
Solution
Leverage Managed ATP

The Brite Way
Our 24/7 expert-managed Open XDR platform reduces alert fatigue by intelligently prioritizing the noise, significantly improving MTTD and MTTR. By leveraging AI and machine learning, we rapidly identify and mitigate potential breaches across your attack surface, providing a unified platform that enhances visibility and tool control while minimizing complexity and costs.
Key Components of Advanced Threat Protection
Next-gen perimeter defense (firewall, secure web gateway)
Advanced network security that proactively blocks threats at the network edge.
Advanced endpoint protection (EDR, MDR, SWG)
Comprehensive device-level security that detects, responds to, and prevents advanced threats in real-time.
Email security
Multi-layered protection against phishing, malware, and other email-borne threats to safeguard sensitive information.
Anomaly detection (anti-bot)
AI-driven system that identifies and mitigates unusual network behavior and bot activities.
Incident response and remediation
Rapid threat containment and system recovery processes to minimize damage from security breaches.
Advanced forensics and event analysis (SIEM, XDR)
Centralized platform for collecting, analyzing, and correlating security data across the entire IT infrastructure to detect and respond to complex threats.
Driving Exceptional Results
Challenge
Lack of In-house Expertise & Support
Solution
Access Expert Cybersecurity Professionals

The Brite Way
Our team of seasoned cybersecurity professionals provides cost-effective expertise without the overhead of building an in-house SOC, continuously adapting our defenses to protect against both current and emerging threats. Whether co-managed or fully managed, we’re always on the other end of the line.
Learn More About Our Advanced Threat Protection Services Today
ATP Featured Insights and Resources

Proactive Cybersecurity Defense: 6 Enhancing Tips
Cyberattacks affect businesses of all types and sizes. Many organizations struggle with prioritizing cybersecurity defense effort and projects. No one is safe from crippling attacks ranging from phishing, malware, insider threats and don’t forget ransomware! The common denominator of all cyber incidents is its ability to hinder productivity, revenue growth and customer satisfaction. These 3…

Cookies, Presents and Identity Theft?
How to survive the season of phishing attacks Cookies, presents, full parking lots and the endless stream marketing emails selling you the best deal. It’s those little things that make the holiday season what it is. What isn’t in the holiday spirit are hackers and phishing campaigns stealing personal and financial information. No one is asking…

The New Generation of Criminals
You turn on your computer and find a notice that all your files have been encrypted and will be destroyed unless you pay a ransom. There’s a clock ticking down the seconds. Your files are being held hostage and so is your organization. Paying ransom is the least of your worries; the biggest cost to your business will be the…