Challenge
Misconfiguration
Solution
Regular Scans and Prioritized Recommendations

The Brite Way
BriteProtect addresses the number one attack vector—software vulnerability exploits—by conducting regular scans and providing prioritized recommendations for remediation. Many organizations struggle to allocate resources for this critical task, but our tactical scans identify and address the most impactful vulnerabilities efficiently to help you plug security gaps effectively.
How Can Brite Help With Vulnerability?
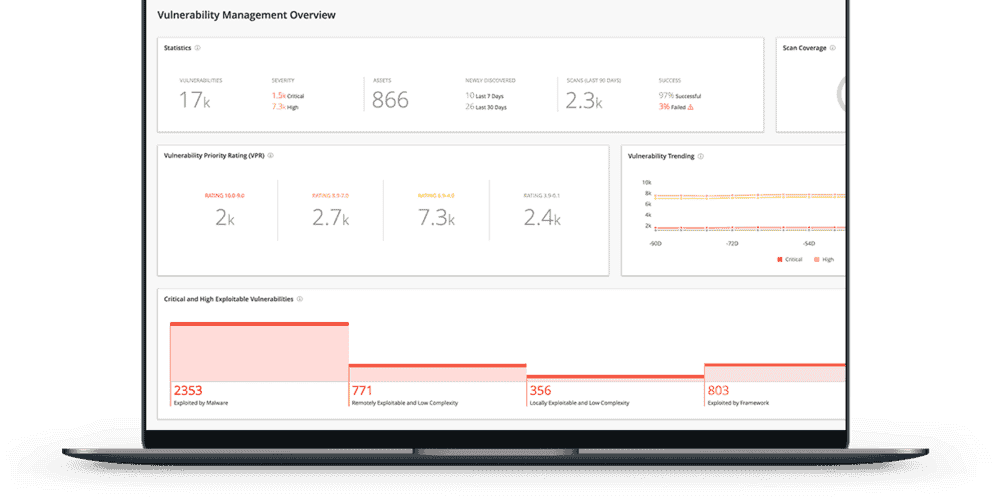
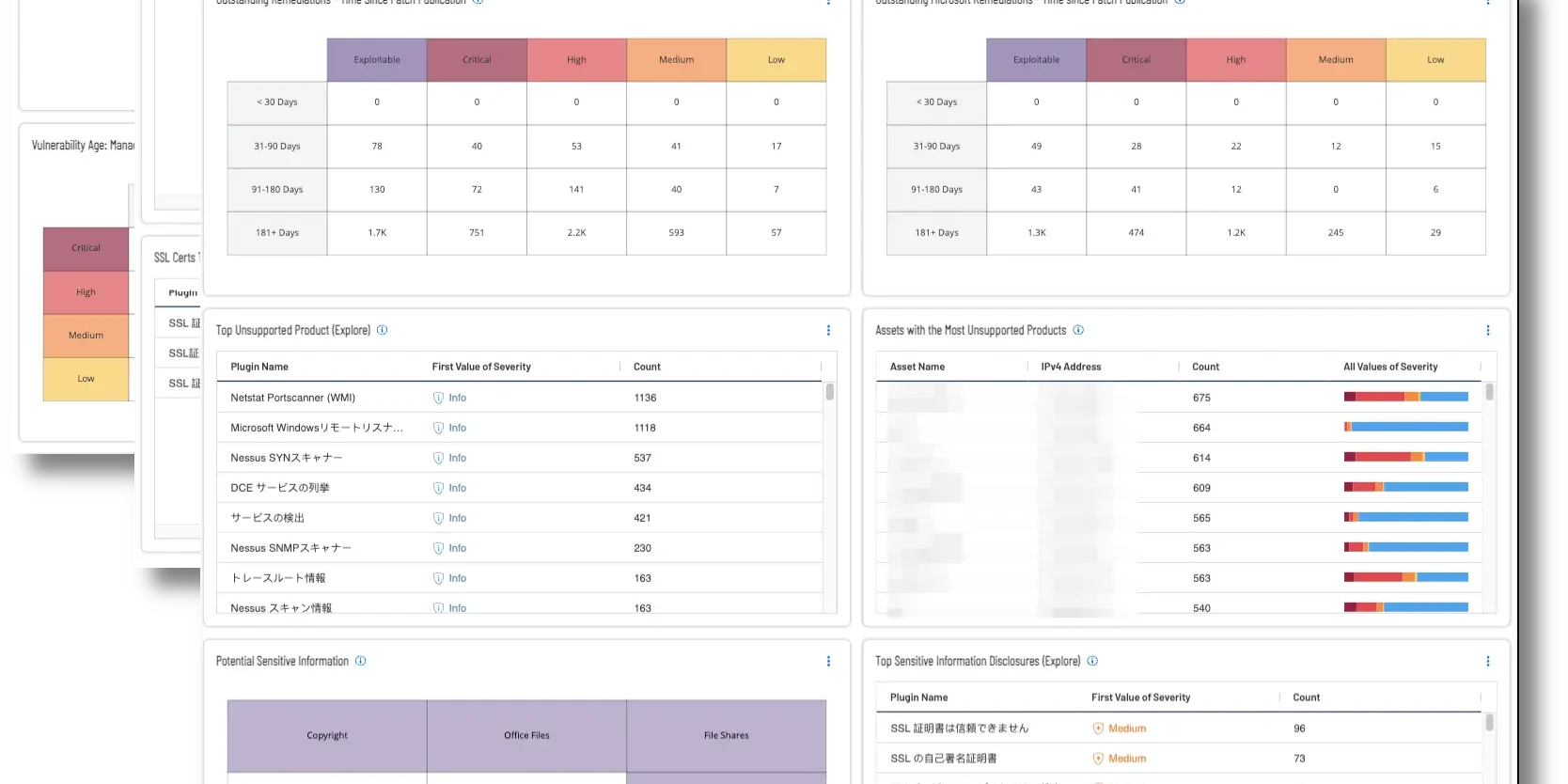
Regular Vulnerability Scans
BriteProtect uses Tenable for weekly vulnerability scans, providing insights that go beyond regulatory compliance. Our scans track both positive and negative changes in your environment, keeping you informed about your security posture.
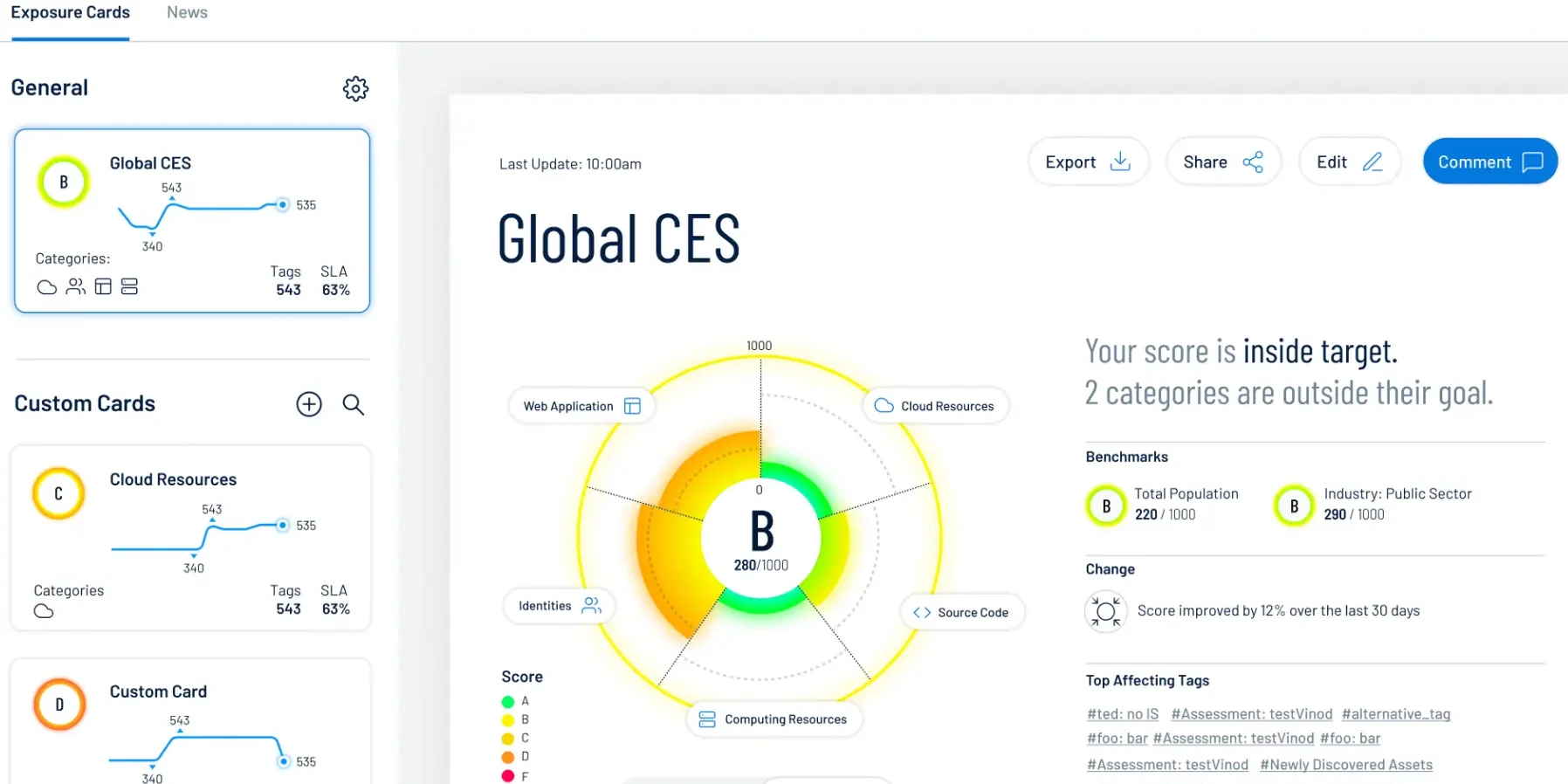
Actionable Risk Assessment Report
Our analysts review each scan, combining insights from your environment with industry trends to deliver a clear, actionable list of vulnerabilities, ensuring effective prioritization.
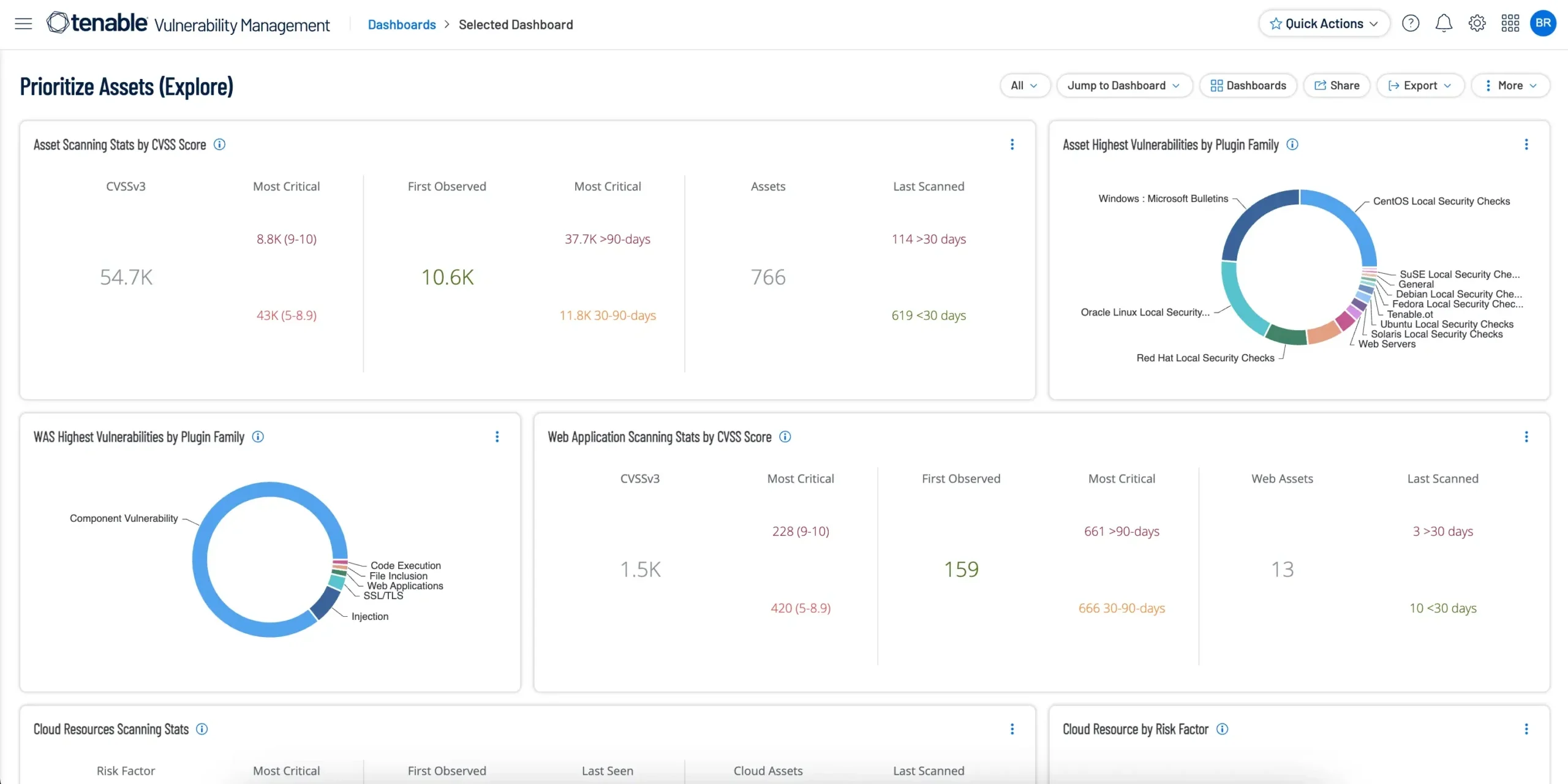
Prioritized List of Vulnerabilities
We provide a concise, prioritized list of vulnerabilities based on business impact, eliminating the overwhelm of lengthy reports and focusing your efforts where they matter most.
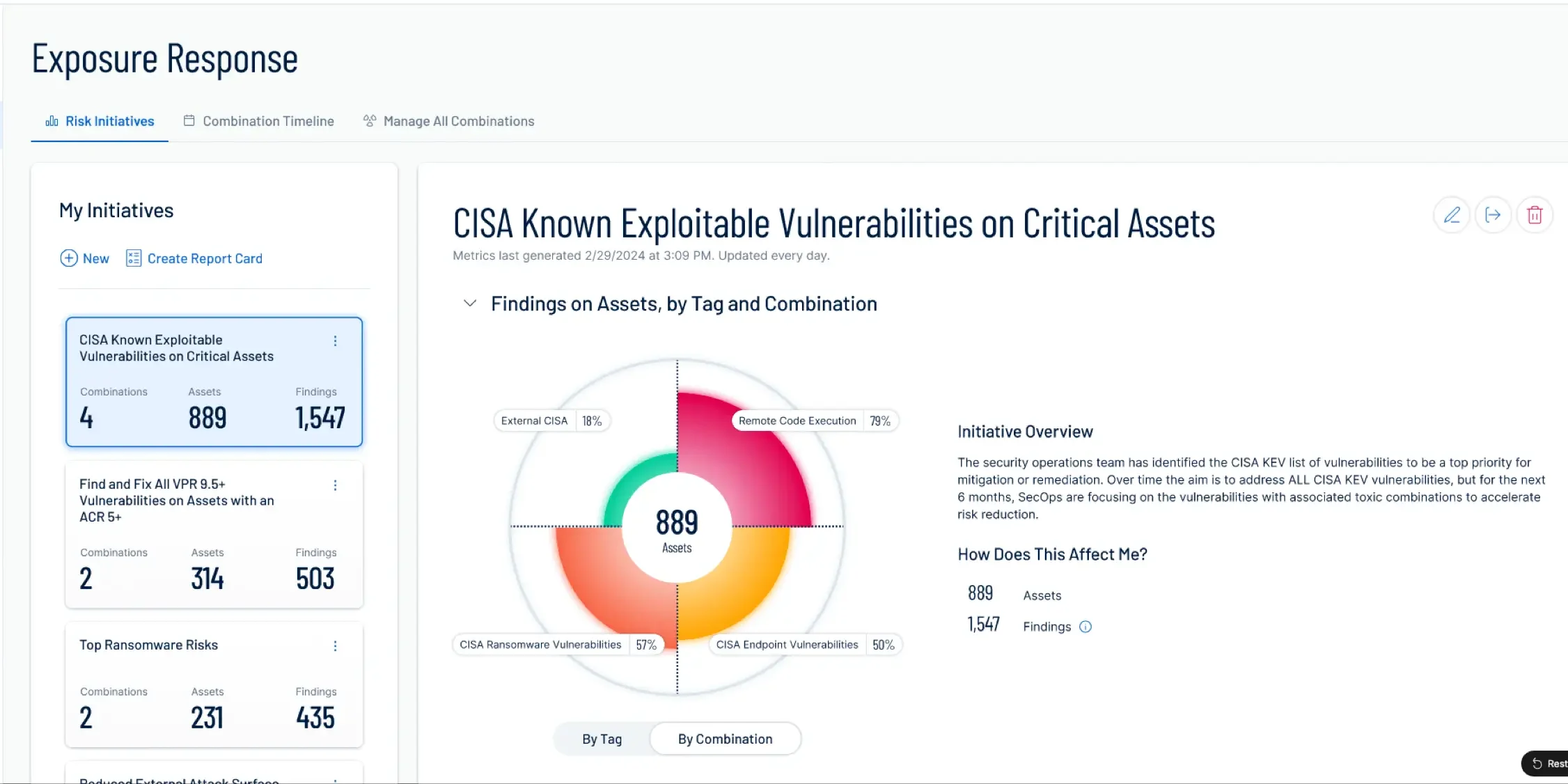
Actionable Remediation Steps
Receive comprehensive remediation steps for high-priority vulnerabilities, allowing you to secure your environment confidently and see measurable improvements through weekly scans.
Patch Management and Remediation Services
Enhance your vulnerability management with BriteStar, our managed IT service that offloads patching and remediation tasks to our expert team, freeing you to focus on strategic initiatives.
Challenge
Outdated or Unpatched Software
Solution
Provide a View of Entire Attack Surface

The Brite Way
BriteProtect’s vulnerability management services offer a comprehensive, risk-based view of your entire attack surface, including IT, cloud, OT, and containers. Our team analyzes results, prioritizes vulnerabilities, and guides remediation, allowing you to focus on the areas that matter most. This proactive approach enhances productivity and strengthens your defenses.
Vulnerability Services
Continuous Scans
Regular weekly vulnerability scans to track changes and maintain an up-to-date view of your security posture.
Vulnerability Prioritization
Concise, prioritized list of vulnerabilities based on business impact, focusing efforts on the most critical issues.
Actionable Remediation
Comprehensive remediation steps for high-priority vulnerabilities, enabling confident security improvements and measurable progress.
Driving Exceptional Results
Get Expert Vulnerability Management Support Today
Brite’s Exposure Management Success Stories
Rapidly Growing Healthcare Company in Need of a True Cybersecurity Program
CHALLENGE
A growing long-term care pharmacy in New York faced a very common challenge of many healthcare organizations: lack of expertise in the demanding area of cybersecurity.
SOLUTION
Brite was able to assist the organization in several ways, including providing vulnerability scans and 24/7 monitoring and management of its environment.
RESULTS
The scans helped to increase visibility and identify latent risks, and the company is now benefiting from a full team of cybersecurity professionals always protecting their environment.
Featured Resources

CVE Management: Removing CVEs Swept Under the Rug
IT leadership builds and manages strong, diverse teams to ensure secure and stable operations. However, sometimes departments overlap resulting in confusion and miscommunication. Such is the case with networking and security departments when it comes to CVE management. It is important to address responsibility early on. Who should be held accountable for any unpatched known…

Comparing Technology Solutions with CVEs
Your organization has a well-planned security strategy. The perimeter and devices are protected. End users are trained. Critical data is safeguarded. With the immense effort and expense of securing an environment, why would anyone still leave the metaphorical front door open to known vulnerabilities? The ease of use of the MITRE Corporation’s publicly available CVE…

Understanding Risk-based Vulnerability Management
Devices, tools and users are constantly being added to your network and widening the attack surface. Every new addition adds another possibility for misconfiguration and vulnerabilities. The longer a vulnerability goes undetected, the greater the risk. Sound familiar? Security teams across industries all live this reality every day. That’s where risk-based vulnerability management can help.…



