Challenge
A Legacy Approach Fails the Modern Workforce
Solution
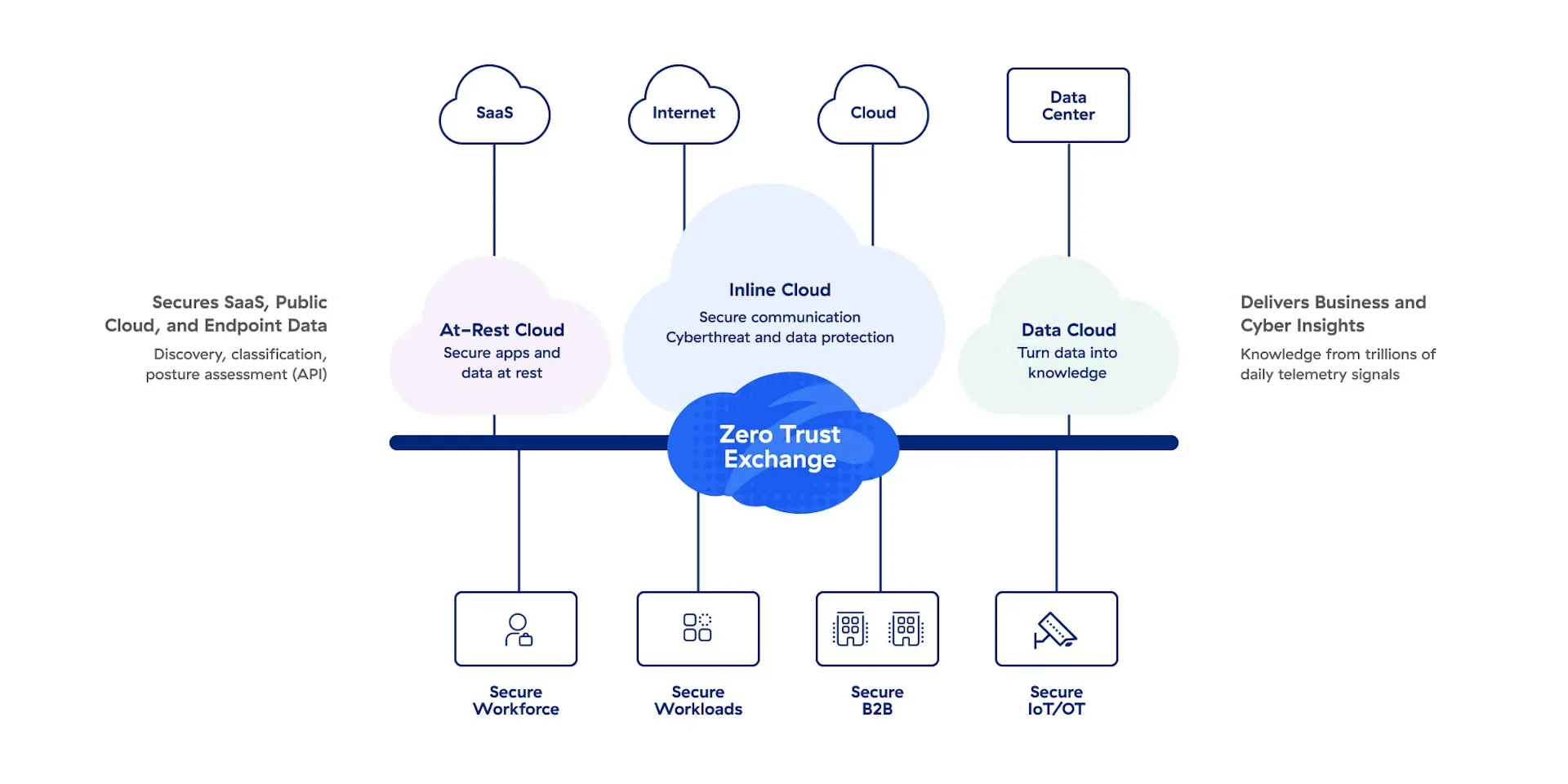
Zero Trust Delivery Platform

The Brite Way
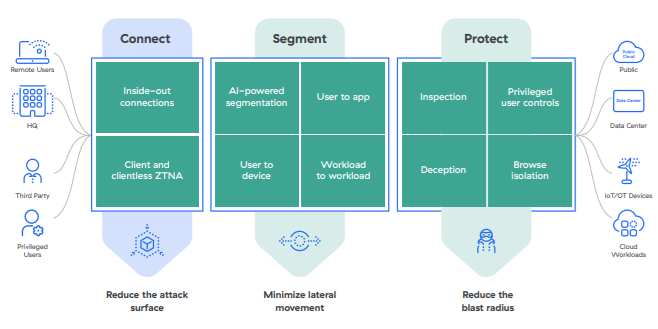
The Brite way emphasizes a holistic approach to security that integrates Zscaler’s Zero Trust principles across all access points. Our platform ensures that every user and device is continuously verified, minimizing the attack surface and preventing unauthorized access. This proactive strategy not only enhances security but also provides a better user experience.
Why Should You Use Our Zero Trust Solutions?
Modern Workplace Enablement
Provide employees, partners, customers, and suppliers with secure access to applications from anywhere on any device.
Infrastructure Modernization
Protect cloud workloads and cloud/SaaS data with zero trust connectivity, segmentation, and posture control.
Security Transformation
Ensure zero trust Internet access for loT (Internet of Things) and OT (Operational Technology) devices and privileged remote access to OT devices.
Challenge
Evolving Cloud Transformation
Solution
Cloud Security Posture Management

The Brite Way
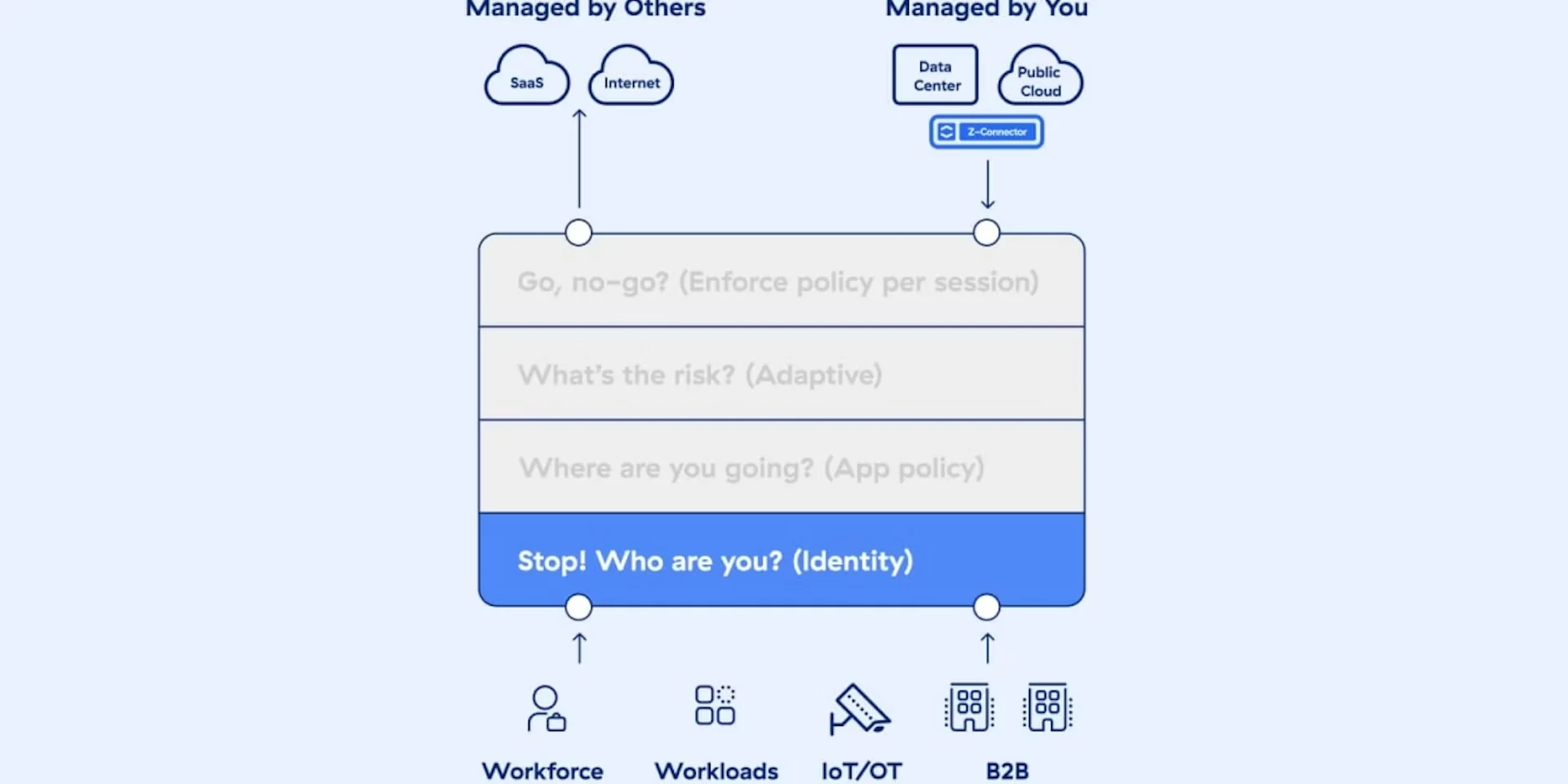
Leveraging a zero-trust framework, our approach ensures that users can securely connect to applications without exposing the underlying network infrastructure. This method provides seamless and secure access regardless of user location, effectively supporting cloud transformation initiatives while maintaining robust security posture management.
Challenges Organizations Solve with Zscaler
Changing Landscape of Cloud Adoption
Brite helps you navigate these changing landscapes with a Zero Trust framework, ensuring secure connections without exposing network infrastructure.
How to Secure Remote Workers
By implementing a Zero Trust model, Brite secures remote workers with robust identity verification, device compliance checks, and secure access protocols.
The Need to Prevent Data Loss
We help you adopt a holistic security approach that integrates Zero Trust principles across all access points to minimize the attack surface and prevent unauthorized access.
Enhancing Overall User Experience
Brite provides seamless and secure access to applications from anywhere on any device, improving user experience while maintaining strong security measures.
Driving Exceptional Results
Challenge
Expanding Attack Surface
Solution
Attack Surface Reduction

The Brite Way
Our approach combines continuous monitoring and automated vulnerability assessments with a zero-trust framework, ensuring that every access request is verified and that potential entry points are minimized. By leveraging advanced analytics and tailored security policies, we help you reduce risk and manage your attack surface.
Learn More About Our Zero Trust Services Today
Featured Resources

How to Create a Zero Trust Architecture
If you’ve made it to part three of our zero trust series, then congratulations you’ve uncovered what zero trust is and have planned your zero trust strategy. With those steps completed, it is time to get to work on how to create a zero trust architecture. Unfortunately, since every organization has its own environment and…

The Guide to Planning a Zero Trust Strategy
“Never trust, always verify” is the zero trust concept and modern-day approach to combatting cyberattacks. In part one of our zero trust series, we uncovered the what and why of zero trust. Naturally, it is time to dive into the how and learn the four steps to planning a zero trust strategy. Since zero trust…

What is Zero Trust, Actually?
There are three guarantees in cybersecurity: ransomware attacks, changing perimeters and new buzzwords. For the last decade, zero trust has been the buzzword of what every security team, tool, approach and framework should be achieving. Now in 2021, we’re seeing an onslaught of ransomware, work environments still in flux with Forrester, NIST and everyone in-between…





