I Clicked on a Phishing Email, Now What?
June 23, 2021
Do you think you clicked on a phishing email? These emails are designed to take advantage of human instinct and emotions. So often at first glance, an email attack looks unsuspecting and creates a high likelihood that unsuspecting victims will act like clicking on a link. Making the stealth tactics extremely successful.
If you clicked on a phishing email, here’s what to do (Spoiler: Tell IT ASAP).
Identify phishing emails
The picture below highlights all the different warning signs of a phishing email. As the end-user, we must check each area to confirm the legitimacy before acting on an email. Sender addresses, generic openings, urgency, multiple grammar mistakes, URLs all make the checklist.
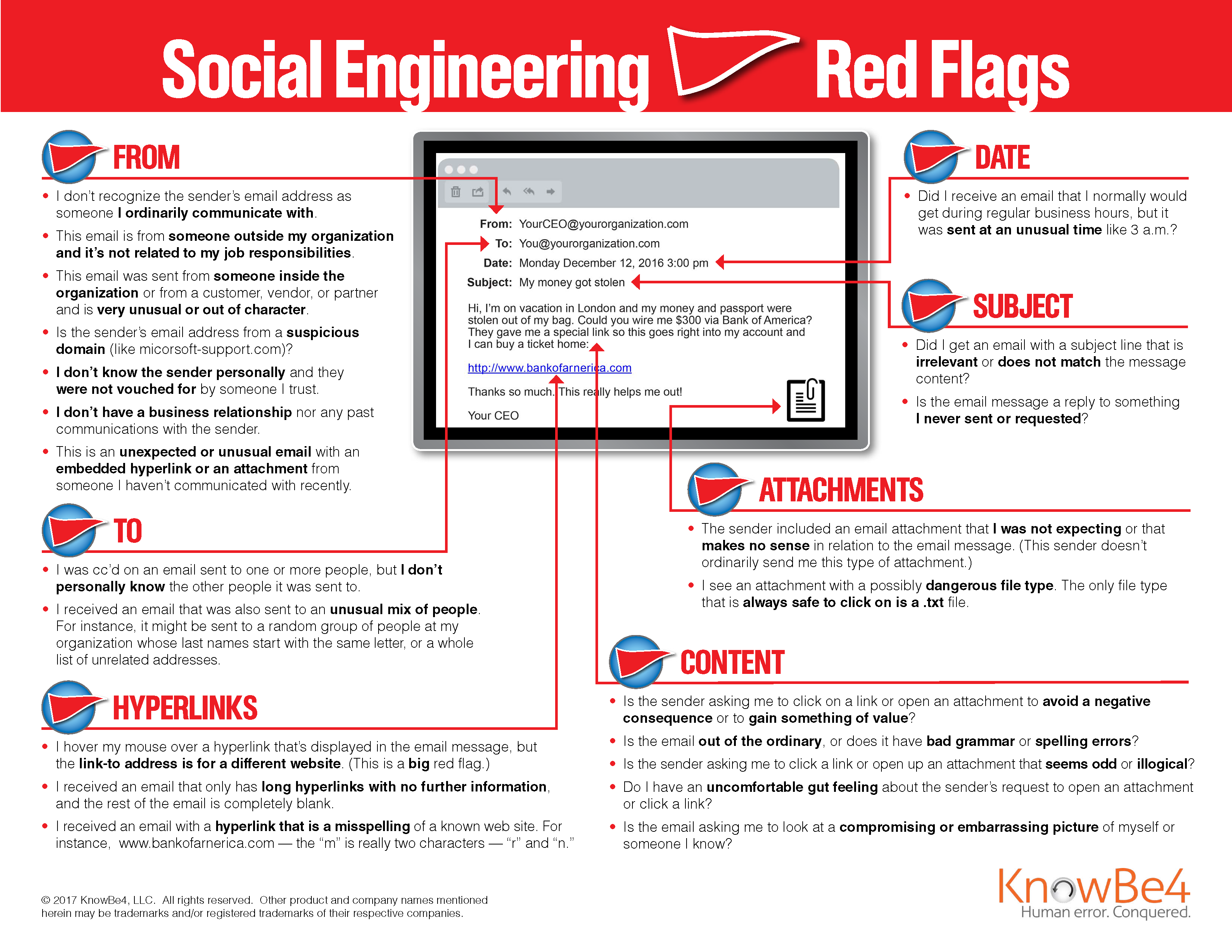
Open vs. clicking a phishing email
Does opening a phishing email create the same threat as clicking a link? Not necessarily. However, it does acknowledge that you and/or the organization are targets of such attacks. As a result, you should still inform the IT team of what happened to take preventative measures going forward.
Brite’s phishing expert and security engineer shared his thoughts, “You receive email messages all day, so you have a sense of what should be normal workflow and content within your mailbox. If something seems unusual or uncommon, contact your IT department. An ounce of prevention can save the day, operations and money.”
What to do if you click on a phishing email
Unfortunately, it can (and will) happen. If you click a link, open an attachment, or even reply to a phishing attack, it’s deemed a successful attack. The next steps are critical and time-sensitive.
- Disconnect the device from the internet immediately. This prevents the attackers from gaining further access to the network and creating damage.
- Inform the IT department immediately. Bringing the attack to their attention allows them to investigate and scan for malware. Additionally, they know that the company is being targeted for attacks and can be proactive about others.
- Change credentials. Update all login usernames and passwords according to best practices. Prioritize changing email and banking accounts as an added protection to cover sensitive information.
- Revert to a backup. If the attack is successful and attackers hold information for ransom, they lose the upper hand and power when you have safe copies of the data.
What’s the most important step?
From Brite’s security engineer, “The most important step is you. Remember, your company has invested heavily in solutions to protect the business from hackers and bad actors. If you get a phishing email that comes through, it has successfully bypassed all those countermeasures. You are the last line of defense. So being able to spot phishing emails makes you just as critical to your IT department as any appliance or software.”
Overall, if you click on a phishing link, don’t panic. Take the device offline and call IT so they can step in and help walk you through the right steps. Not acting means that attackers can infiltrate the network, stealing data or stopping operations with a ransomware demand – creating more damage.

Posted in Cybersecurity, Managed Services
